Displaying items by tag: EC3
EUROPOL RELEASED ITS SERIOUS AND ORGANISED CRIME THREAT ASSESSMENT 2021
12 Apr 2021, Europol publishes the European Union (EU) Serious and Organised Crime Threat Assessment, the EU SOCTA 2021. The SOCTA, published by Europol every four years, presents a detailed analysis of the threat of serious and organised crime facing the EU. The SOCTA is a forward-looking assessment that identifies shifts in the serious and organised crime landscape.
The SOCTA 2021 details the operations of criminal networks in the EU and how their criminal activities and business practices threaten to undermine our societies, economy and institutions, and slowly erode the rule of law. The report provides unprecedented insights into Europe’s criminal underworld based on the analysis of thousands of cases and pieces of intelligence provided to Europol.
The SOCTA reveals a concerning expansion and evolution of serious and organised crime in the EU. The document warns of the potential long-term implications of the COVID-19 pandemic and how these may create ideal conditions for crime to thrive in the future. The report clearly highlights serious and organised crime as the key internal security challenge currently facing the EU and its Member States.
Launched at the Portuguese Police’s headquarters (Policia Judicária) in Lisbon during the Portuguese Presidency of the Council of the European Union, the SOCTA 2021 is the most comprehensive and in-depth study of serious and organised crime in the EU ever undertaken.
THE MOST PRESSING INTERNAL SECURITY THREAT TO THE EU
EU citizens enjoy some of the highest levels of prosperity and security in the world. However, the EU still faces serious challenges to its internal security, threatening to undo some of our common achievements and undermine shared European values and ambitions. As the EU is facing the COVID-19 pandemic, one of the most significant crises since the end of World War II, criminals seek to exploit this extraordinary situation targeting citizens, businesses, and public institutions alike.
The analysis presented in the SOCTA 2021 highlights key characteristics of serious and organised crime such as the widespread use of corruption, the infiltration and exploitation of legal business structures for all types of criminal activity, and the existence of a parallel underground financial system that allows criminals to move and invest their multi-billion euro profits.
Serious and organised crime encompasses a diverse range of criminal phenomena ranging from the trade in illegal drugs to crimes such as migrant smuggling and the trafficking in human beings, economic and financial crime and many more.
Key findings of the SOCTA 2021:
- Serious and organised crime has never posed as high a threat to the EU and its citizens as it does today.
- The COVID-19 pandemic and the potential economic and social fallout expected to follow threaten to create ideal conditions for organised crime to spread and take hold in the EU and beyond. Once more confirmed by the pandemic, a key characteristic of criminal networks is their agility in adapting to and capitalising on changes in the environment in which they operate. Obstacles become criminal opportunities.
- Like a business environment, the core of a criminal network is composed of managerial layers and field operators. This core is surrounded by a range of actors linked to the crime infrastructure providing support services.
- With nearly 40 percent of the criminal networks active in drugs trafficking, the production and trafficking of drugs remains the largest criminal business in the EU.
- The trafficking and exploitation of human beings, migrant smuggling, online and offline frauds and property crime pose significant threats to EU citizens.
- Criminals employ corruption. Almost 60% of the criminal networks reported engage in corruption.
- Criminals make and launder billions of euros annually. The scale and complexity of money laundering activities in the EU have previously been underestimated. Professional money launderers have established a parallel underground financial system and use any means to infiltrate and undermine Europe’s economies and societies.
- Legal business structures are used to facilitate virtually all types of criminal activity with an impact on the EU. More than 80% of the criminal networks active in the EU use legal business structures for their criminal activities.
- The use of violence by criminals involved in serious and organised crime in the EU appears to have increased in terms of the frequency of use and its severity. The threat from violent incidents has been augmented by the frequent use of firearms or explosives in public spaces.
- Criminals are digital natives. Virtually all criminal activities now feature some online component and many crimes have fully migrated online. Criminals exploit encrypted communications to network among each other, use social media and instant messaging services to reach a larger audience to advertise illegal goods, or spread disinformation.
The SOCTA 2021 assists decision-makers in the prioritisation of serious and organised crime threats. It is a product of close cooperation between Europol, EU Member States law enforcement authorities, third parties such as EU agencies, international organisations, and countries outside the EU with working arrangements with Europol. These crucial stakeholders’ involvement is also reflected in the SOCTA’s role as the cornerstone of the European Multidisciplinary Platform Against Criminal Threats (EMPACT) in the EU.
$ 400M INVESTMENT SCAM - FENITA LA COMEDY FINIKO
The illegal Finiko service started operating at the end of 2017. It was positioned as an automatic profit-making system. Currently, it is represented by Cyfron FNK LTD, registered in the state of Saint Lucia (no license is required to work with cryptocurrencies).
The site in the .ru domain zone is not available. There is a working mirror of “thefiniko” (in the .com zone). The user agreements on both sites are identical. What is noteworthy is that the platform offers gaming programs that mimic investment programs. And the internal CFR token is not an official currency and has no financial value. The company does not bear any responsibility.
This approach allows Finiko to work without loss since 2017. In November 2018, the platform launched an active advertising campaign. The scammers offered to buy an apartment or a car, pay off another loan for 35% of the cost. The peak of active use of the service occurred at the end of 2019. This was accompanied by the visibility of the accrual of funds to users. However, few users were able to withdraw real funds...
There are the main signs of a financial pyramid: lack of regulation, registration in an offshore company, short life (the cost of the CFR token is close to zero), very high profitability (promised more than 200% per year), enticing and expensive website design, a lot of good reviews.
Finiko, the only known cryptocurrency, has a huge number of wallets in Bitcoin and Ethereum. The largest crypto wallet received 12099.294 BTC (almost in 2.5 years). It may have been used for trading on the stock exchange. More than 129 thousand wallets involved in the activities of the illegal service have been identified. The main large (used for receiving / sending) wallets are monitored by the services of the SICP platform.
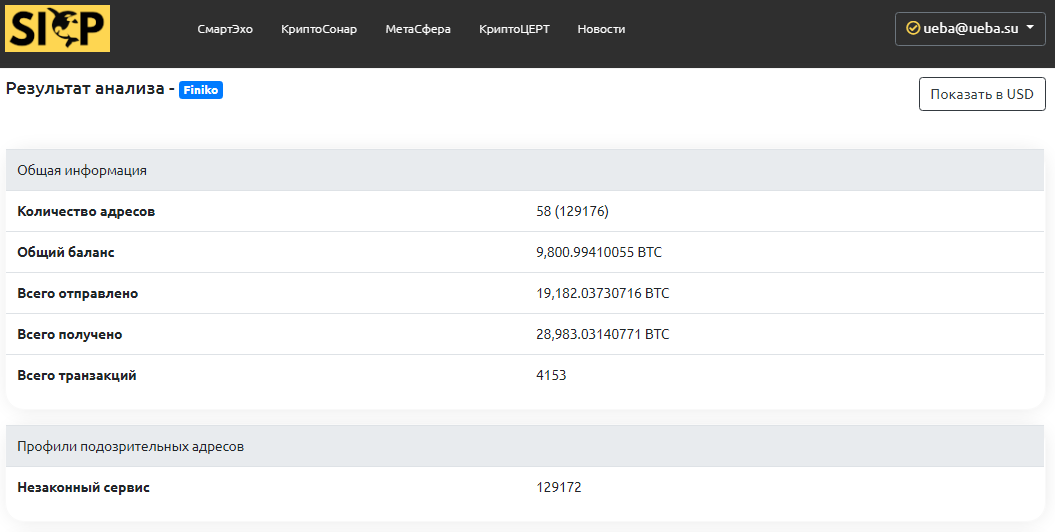
In the darknet, there is a forum where enthusiasts are working to identify large Finiko wallets and select private keys to them. In total, Finiko attracted more than $300 million from the population (according to SICP experts, more than $400 million)!..
Analysis of recent transactions shows that the funds are withdrawn mainly on the Asian cryptocurrency exchange, managed from Russia. If you or your loved one suffered from the activities of Finiko, please contact CryptoCERT (This email address is being protected from spambots. You need JavaScript enabled to view it.).
Source: sicp.ueba.su
INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA) 2019
The European Union Agency for Law Enforcement Cooperation, or Europol, 09/10/2019 released its annual Internet Organized Crime Threat Assessment (IOCTA) report for the year. And we weren’t surprised to find that ransomware, despite its palpable decline in volume these past few months—a trend we’ve also seen and documented—remains the most prominent threat in terms of prevalence and financial damage.
While the IOCTA report talks about online threats that both consumers and businesses face on a daily basis, it also puts data at the center of it all. We rely on it—often, all too much—and criminals know this. And yet, most threat actors behind attack campaigns rely on our data to make their attacks more successful, compelling us to take action. After all, nowadays an attack that doesn’t use data against its owners wouldn’t be much of a money-earning scheme.
Threat actors can deprive organizations and individuals’ access to their own files by encrypting and holding them for ransom, such is the case for ransomware. And they can also deny the average user access to an organization’s data (and services) through Distributed Denial of Service (DDoS) attacks. According to Europol, such attacks with an extortion element in them are the most prevalent.
Data also enables other forms of online crime like fraud. Criminals are primarily after financial data, such as credit card information, online banking credentials, and cryptocurrency wallet data. They are also after personally identifiable information (PII) and other login credentials. Such data fuels other profitable, targeted attacks like business email compromise (BEC) scams, spear phishing, and account takeovers.
There is also the challenge of data overload, particularly in the realm of child sexual exploitation (CSE) crimes. The staggering amount of material online detected by law enforcement and private companies continues to increase to the point that it’s putting a strain on law enforcement resources to investigate these crimes. One contributing factor to the increase of availability of CSE material online is that more underage users are accessing and using social media, thus, criminals reach and communicate with them via these platforms.
Other IOCTA findings:
- The IOCTA report also noted that key infection vectors are phishing and remote desktop protocol (RDP) vulnerabilities. Simple patching can address vulnerabilities. As for phishing, did you know that you can be targeted on your desktop and smart phone?
- Organizations are growing more concerned about sabotage performed by malicious insiders.
- Ransomware tactics have shifted, from a scattergun approach of infecting systems to a more focused and refined targeting of profitable victims. This means that ransomware proponents target those with a greater ability to pay a ransom than the average, normal user.
- BEC is evolving. There have been campaigns wherein threat actors used malware and network intrusion.
- Self-generated explicit material (SGEM) is on the uptick. Young children now have access to high-quality smart phones, which enables them to produce and share SGEM, either voluntarily or under coercion. The rising number of SGEM victims will likely to continue. Parents and guardians: Please talk to your kids about this, and other online risks.
- Jackpotting, also known as black-box attacks, against ATMs are becoming more widespread and accessible due to tools like Cutlet Maker being more available on the dark web.
- Card-not-present (CNP) fraud and skimming continue to plague financial institutions. Don’t be a victim of skimming.
- Due to law enforcement activity and extensive DDoS attacks against hidden services, many have grown distrustful of the onion router (Tor) environment. While underground market administrators are currently exploring alternatives, a migration to a new platform will not likely happen yet.
Source: Europol
Source: Malwarebytes Labs
О КОСАтка
Корпоративная система аналитики Транзакция Криптовалюта Актив - кибербезопасность инфраструктуры блокчейнов и антифрод в криптовалютной сфере (антискам, прозрачность, комплаенс).
Связаться
Российская Федерация, Москва
Тел.: +7 (911) 999 9868
Факс:
Почта: cosatca@ueba.su
Сайт: www.ueba.su